Wide Area Network
Wide Area Networks (WANs) connect larger geographic areas, such as Florida, the United States, or the world. Dedicated transoceanic cabling or satellite uplinks may be used to connect this type of network.
Using a WAN, schools in Florida can communicate with places like Tokyo in a matter of minutes, without paying enormous phone bills. A WAN is complicated. It uses
- Speed. Networks provide a very rapid method for sharing and transferring files. Without a network, files are shared by copying them to memory cards or discs, then carrying or sending the discs from one computer to another. This method of transferring files (referred to as sneaker-net) can be very time-consuming.
- Cost. Networkable versions of many popular software programs are available at considerable savings when compared to buying individually licensed copies.
- Security. Files and programs on a network can be designated as "copy inhibit," so that you do not have to worry about illegal copying of programs. Also, passwords can be established for specific directories to restrict access to authorized users.
- Centralized Software Management. One of the greatest benefits of installing a network at a school is the fact that all of the software can be loaded on one computer (the file server). This eliminates that need to spend time and energy installing updates and tracking files on independent computers throughout the building.
- Resource Sharing. Sharing resources is another advantage of school networks. Most schools cannot afford enough laser printers, fax machines, modems, scanners, and CD players for each computer. However, if these or similar peripherals are added to a network, they can be shared by many users.
- Electronic Mail. The presence of a network provides the hardware necessary to install an e-mail system. E-mail aids in personal and professional communication for all school personnel, and it facilitates the dissemination of general information to the entire school staff. Electronic mail on a LAN can enable students to communicate with teachers and peers at their own school. If the LAN is connected to the Internet, students can communicate with others throughout the world.
- Flexible Access. School networks allow students to access their files from computers throughout the school. Students can begin an assignment in their classroom, save part of it on a public access area of the network, then go to the media center after school to finish their work. Students can also work cooperatively through the network.
- Workgroup Computing. Collaborative software allows many users to work on a document or project concurrently. For example, educators located at various schools within a county could simultaneously contribute their ideas about new curriculum standards to the same document, spreadsheets, or website.
Disadvantages of Installing a Network
- Expensive to Install. Although a network will generally save money over time, the initial costs of installation can be prohibitive. Cables, network cards, routers, and software are expensive, and the installation may require the services of a technician.
- Requires Administrative Time. Proper maintenance of a network requires considerable time and expertise. Many schools have installed a network, only to find that they did not budget for the necessary administrative support.
- File Server May Fail. Although a file server is no more susceptible to failure than any other computer, when the files server "goes down," the entire network may come to a halt. When this happens, the entire school may lose access to necessary programs and files.
- Cables May Break. The Topology chapter presents information about the various configurations of cables. Some of the configurations are designed to minimize the inconvenience of a broken cable; with other configurations, one broken cable can stop the entire network.
- Must Monitor Security Issues. Wireless networks are becoming increasingly common; however, security can be an issue with wireless networks.
1.4 Introduction to Network Components
We have discussed a network, at its simplest, is anything that enables two or more computers to communicate with each other and or other devices. This enables users to use computers and networking to share information, collaborate on a work item, print, and even communicate directly through individually addressed messages.
Networks consist of many components, including both hardware and software. Some f components can even be completely intangible.
Before we go too far into the basic network components, it's important to note that networks have evolved into three categories; local area networks (LANs), wide area networks (WAN) and Metropolitan area networks (MAN).If we classify a network based on the area coverage.
Note: A third category of network is the metropolitan area network (MAN). Although defined through the IEEE's project 802, the same initiative that standardized LANs, MANs are more closely related to WANs than LANs, They remain relatively obscure and are seldom used.
1. Hardware components
The basic hardware components of a network include three types of devices:
- Transmission facilities
- Access devices
- Devices that repeat transmitted signals
These components are basic in that all networks must either contain them or, at a minimum work around them
Transmission facilities: -Transmission facilities are the media used to transport a network's signal to their destination. Media types can include coaxial cables, twisted pair, and even fiber-optic cabling
LAN media types can also be intangible. They can be light, radio, and even microwave signal, transmitted through open air. Although the atmosphere, itself, is the actual media used to support these various forms of transmission. 1t's more useful to describe the mechanisms that generate the transmissions than it is to describe the air that carries the transmissions. We will discuss the more common LAN transmission media in further detail in the next sections.
The WAN, has its own transmission facilities. Such facilities are often thought of in terms of their clock rates and frame structures rather than simple transmission media (a 1.544Mbps Frame Relay leased line, for example). Their physical media are inconsequential to their actual performance.
Access devices Some of the functions of access devices are the following
Properly formatting data so that it can be accepted in the network
Placing that data on the network
Accepting transmitted data that's addressed to it
In a local area network, the access device is known as a network interface card (NIC). The NIC is a circuit board that's installed in a computer and occupies an I/O slot on the motherboard. The network is then cabled to the port provided by this board. The NIC frames data that the computer's applications need to transmit, puts that data onto the network in binary form, and -accepts inbound frames that are addressed to that computer.
In a wide area network, the access device is a router. Routers operate at Layer 3 of the OSI = Reference model and include two types of protocols: routing and routable. Routable protocols, such as IP, are used to transport data beyond the boundary of Layer 2 domains.
Routing protocols provide all the functions necessary to perform the following tasks:
- Determine optimal paths through a WAN, for any given destination address
- Accept and forward packets through those paths to their destinations
Repeaters
A repeater is a device that accepts transmitted signals, amplifies them, and puts them back on the network. In a LAN, a repeater is more popularly referred to as a hub enables multiple devices to be networked together by providing multiple ports to the network. This function is so critical to today's LANs that its real purpose-signal regeneration-is often forgotten.
The hub's capability to regenerate signals is every bit as crucial to the success of a LAN as its capability to provide ingress points. The inescapable reality is that the media that transports them affects transmitted signals. Electronic signals placed on a wire inevitably deteriorate. This deterioration can take one of two possible forms: attenuation or distortion.
Attenuation is a decrease in the strength of the signal- Distortion is the unwanted modification of signals in transit. Each of these forms of deterioration must be addressed and rectified separately.
Attenuation can be compensated by keeping wire length short enough to guarantee that; the signal is strong enough to reach all destinations on the wire. If the wire must be relatively lengthy, however, a repeater can be installed in the line.
Distortion is a more severe problem for signal transmission. This is different from attenuation. Distorted signals corrupt whatever data is being transported. Repeaters are incapable of differentiating legitimate signals from distorted ones; they repeat signals indiscriminately. There are, however, several other ways to combat distortion:
- Adhere rigidly to any installation guidelines that may have been provided with your transmission media.
- Identify all causes 0 f t he distortion. Next, try to route cabling away from those sources. Also, it may be beneficial to use network transmission technologies, such as fiber-optic cabling, that can resist that distortion.
- Use' network protocols that are capable of detecting and automatically correcting any n. transmission errors that may occur. Software components
What is Networking Hardware?
Networking hardware includes all computers, peripherals, interface cards and other equipment needed to perform data-processing and communications within the network. CLICK on the terms below to learn more about those pieces of networking hardware.
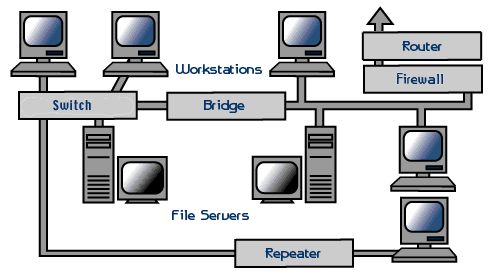
This section provides information on the following components:
File Servers
A file server stands at the heart of most networks. It is a very fast computer with a large amount of RAM and storage space, along with a fast network interface card. The network operating system software resides on this computer, along with any software applications and data files that need to be shared.
The file server controls the communication of information between the nodes on a network. For example, it may be asked to send a word processor program to one workstation, receive a database file from another workstation, and store an e-mail message during the same time period. This requires a computer that can store a lot of information and share it very quickly. File servers should have at least the following characteristics:
- 800 megahertz or faster microprocessor (Pentium 3 or 4, G4 or G5)
- A fast hard drive with at least 120 gigabytes of storage
- A RAID (Redundant Array of Inexpensive Disks) to preserve data after a disk casualty
- A tape back-up unit (i.e. DAT, JAZ, Zip, or CD-RW drive)
- Numerous expansion slots
- Fast network interface card
- At least of 512 MB of RAM
Workstations
All of the user computers connected to a network are called workstations. A typical workstation is a computer that is configured with a network interface card, networking software, and the appropriate cables. Workstations do not necessarily need floppy disk drives because files can be saved on the file server. Almost any computer can serve as a network workstation.
Network Interface Cards
The network interface card (NIC) provides the physical connection between the network and the computer workstation. Most NICs are internal, and they are included in the purchase of most computers. Network interface cards are a major factor in determining the speed and performance of a network. It is a good idea to use the fastest network card available for the type of workstation you are using.
The most common network interface connections are Ethernet cards (LocalTalk connectors and Token Ring cards are seldom used in current networks).
Ethernet Cards
Ethernet cards are usually purchased separately from a computer, although many computers (such as the Macintosh) now include an option for a pre-installed Ethernet card. Ethernet cards contain connections for either coaxial or twisted pair cables (or both) (See fig. 1). If it is designed for coaxial cable, the connection will be BNC. If it is designed for twisted pair, it will have a RJ-45 connection. Some Ethernet cards also contain an AUI connector. This can be used to attach coaxial, twisted pair, or fiber optics cable to an Ethernet card. When this method is used there is always an external transceiver attached to the workstation. (See the Cabling section for more information on connectors.)
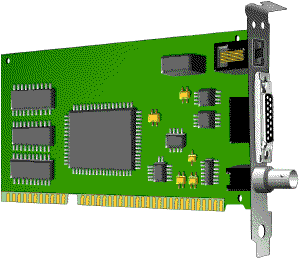
Fig. 1. Ethernet card.
From top to bottom:
RJ-45, AUI, and BNC connectors
LocalTalk Connectors
LocalTalk is Apple's built-in solution for networking older Macintosh computers. It utilized a special adapter box and a cable that plugged into the printer port of a Macintosh. A major disadvantage of LocalTalk was that it is slow (only 230 Kbps) in comparison to Ethernet; therefore, it is rarely used in current networks.
Token Ring Cards
Token Ring network cards look similar to Ethernet cards and were popular in IBM computers. They are seldom used with current networks.
Switches
A concentrator is a device that provides a central connection point for cables from workstations, servers, and peripherals. In a star topology, twisted-pair wire is run from each workstation to a central switch/hub. Most switches are active, that is they electrically amplify the signal as it moves from one device to another. Switches no longer broadcast network packets as hubs did in the past, they memorize addressing of computers and send the information to the correct location directly. Switches are:
- Usually configured with 8, 12, or 24 RJ-45 ports
- Often used in a star or tree topology
- Sold with specialized software for port management
- Also called hubs
- Usually installed in a standardized metal rack that also may store netmodems, bridges, or routers
Repeaters
Since a signal loses strength as it passes along a cable, it is often necessary to boost the signal with a device called a repeater. The repeater electrically amplifies the signal it receives and rebroadcasts it. Repeaters can be separate devices or they can be incorporated into a concentrator. They are used when the total length of your network cable exceeds the standards set for the type of cable being used.
A good example of the use of repeaters would be in a local area network using a star topology with unshielded twisted-pair cabling. The length limit for unshielded twisted-pair cable is 100 meters. The most common configuration is for each workstation to be connected by twisted-pair cable to a multi-port active concentrator. The concentrator amplifies all the signals that pass through it allowing for the total length of cable on the network to exceed the 100 meter limit.
Bridges
A bridge is a device that allows you to segment a large network into two smaller, more efficient networks. If you are adding to an older wiring scheme and want the new network to be up-to-date, a bridge can connect the two.
A bridge monitors the information traffic on both sides of the network so that it can pass packets of information to the correct location. Most bridges can "listen" to the network and automatically figure out the address of each computer on both sides of the bridge. The bridge can inspect each message and, if necessary, broadcast it on the other side of the network.
The bridge manages the traffic to maintain optimum performance on both sides of the network. You might say that the bridge is like a traffic cop at a busy intersection during rush hour. It keeps information flowing on both sides of the network, but it does not allow unnecessary traffic through. Bridges can be used to connect different types of cabling, or physical topologies. They must, however, be used between networks with the same protocol.
Routers
A router translates information from one network to another; it is similar to a superintelligent bridge. Routers select the best path to route a message, based on the destination address and origin. The router can direct traffic to prevent head-on collisions, and is smart enough to know when to direct traffic along back roads and shortcuts.
While bridges know the addresses of all computers on each side of the network, routers know the addresses of computers, bridges, and other routers on the network. Routers can even "listen" to the entire network to determine which sections are busiest -- they can then redirect data around those sections until they clear up.
If you have a school LAN that you want to connect to the Internet, you will need to purchase a router. In this case, the router serves as the translator between the information on your LAN and the Internet. It also determines the best route to send the data over the Internet. Routers can:
The software components required in a network include the following:
ü Protocols that define and regulate the way two or more devices communicate
ü Hardware-level software, known as microcode or drivers, that guide the functionality of individual devices such as network interface cards
ü Communications software
Protocols
Providing the physical connectivity for a network is the easy part. The real challenge lies in developing standard ways for computers, and even other network-attached devices, to communicate. These ways are more formally known as protocols. The simplest example of a protocol can be found in the way that most people communicate over a telephone. In most of the world, the first thing that is said in any phone conversation is "Hello" (or its regional equivalent).
This simple greeting universally conveys that the calling party has successfully established a communications session with someone else. The next step is for the caller to respond (with their own "Hello") so that the recipient of the phone call can tell that the communications link works in both directions.
If both parties are familiar with each other, this simple two-word exchange is usually sufficient to predicate even the most intimate of conversations. If, however, both parties are unknown to each other, additional protocols are needed to establish each other's identity. After this is established, the conversation can move on to the purpose for the call.
This simple example has become so ingrained that violations protocols are often interpreted as a lack of manners or even deliberate rudeness.
Computers are on different. Merely having a network to connect them is only one part of what is needed to support meaningful communications and resources sharing. Direct communications between two computers enables them and their users to share resources. Given that precious few people actually work in isolation, enabling computers to share information and other resources was a revolutionary step toward an information technology infrastructure that more closely approximated the way groups of people actually work.
Protocols for LAN are frequently called LAN architectures, as they are embodies 'in the NIC. They predetermine much of the shape, size, and mechanics of the LAN. Protocols for WANs usually come in bundles and are responsible for a great variety.
What is a Protocol?
A protocol is a set of rules that governs the communications between computers on a network. In order for two computers to talk to each other, they must be speaking the same language. Many different types of network protocols and standards are required to ensure that your computer (no matter which operating system, network card, or application you are using) can communicate with another computer located on the next desk or half-way around the world. The OSI (Open Systems Interconnection) Reference Model defines seven layers of networking protocols. The complexity of these layers is beyond the scope of this tutorial; however, they can be simplified into four layers to help identify some of the protocols with which you should be familiar (see fig 1).
|
OSI Layer
|
Name
|
|
Common Protocols
|
|
7
|
Application
|
|
|
|
6
|
Presentation
|
|
HTTP | FTP | SMTP | DNS
|
|
5
|
Session
|
|
|
|
4
|
Transport
|
|
TCP
|
SPX
|
|
3
|
Network
|
|
IP
|
IPX
|
|
2
|
Data Link
|
|
Ethernet
|
|
1
|
Physical
|
|
Fig 1. OSI model related to common network protocols
Figure 1 illustrates how some of the major protocols would correlate to the OSI model in order to communicate via the Internet. In this model, there are four layers, including:
- Ethernet (Physical/Data Link Layers)
- IP/IPX (Network Layer)
- TCP/SPX (Transport Layer)
- HTTP, FTP, Telnet, SMTP, and DNS (Session/Presentation/Application Layers)
Assuming you want to send an e-mail message to someone in Italy, we will examine the layers "from the bottom up" -- beginning with Ethernet (physical/data link kayers).
Ethernet (Physical/Data Link Layers)
The physical layer of the network focuses on hardware issues, such as cables, repeaters, and network interface cards. By far the most common protocol used at the physical layer is Ethernet. For example, an Ethernet network (such as 10BaseT or 100BaseTX) specifies the type of cables that can be used, the optimal topology (star vs. bus, etc.), the maximum length of cables, etc. (See the Cabling section for more information on Ethernet standards related to the physical layer).
The data link layer of the network addresses the way that data packets are sent from one node to another. Ethernet uses an access method called CSMA/CD (Carrier Sense Multiple Access/Collision Detection). This is a system where each computer listens to the cable before sending anything through the network. If the network is clear, the computer will transmit. If some other node is already transmitting on the cable, the computer will wait and try again when the line is clear. Sometimes, two computers attempt to transmit at the same instant. When this happens a collision occurs. Each computer then backs off and waits a random amount of time before attempting to retransmit. With this access method, it is normal to have collisions. However, the delay caused by collisions and retransmitting is very small and does not normally effect the speed of transmission on the network.
Ethernet
The original Ethernet standard was developed in 1983 and had a maximum speed of 10 Mbps (phenomonal at the time). The Ethernet protocol allows for bus, star, or tree topologies, depending on the type of cables used and other factors .
The current standard at the 10 Mbps level is 10BaseT. The "10" stands for the speed of transmission (10 megabits per second); the "Base" stands for "baseband" meaning it has full control of the wire on a single frequency; and the "T" stands for "twisted pair" cable. Older standards, such as 10Base2 and 10Base5, used coaxial cable, but these standards are seldom used in new installations. Fiber cable can also be used at this level in 10BaseFL.
Fast Ethernet
The Fast Ethernet protocol supports transmission up to 100 Mbps. Fast Ethernet requires the use of different, more expensive network concentrators/hubs and network interface cards. In addition, category 5 twisted pair or fiber optic cable is necessary. Fast Ethernet standards include:
- 100BaseT - 100 Mbps over 2-pair category 5 or better UTP cable.
- 100BaseFX - 100 Mbps over fiber cable.
- 100BaseSX -100 Mbps over multimode fiber cable.
- 100BaseBX - 100 Mbps over single mode fiber cable.
Gigabit Ethernet
Gigabit Ethernet standard is a protocol that has a transmission speed of 1 Gbps (1000 Mbps). It can be used with both fiber optic cabling and copper. The 1000BaseT, the copper cable used for Gigabit Ethernet (see the Cabling section for more information).
- 1000BaseT - 1000 Mbps over 2-pair category 5 or better UTP cable.
- 1000BaseTX - 1000 Mbps over 2-pair category 6 or better UTP cable.
- 1000BaseFX - 1000 Mbps over fiber cable.
- 1000BaseSX -1000 Mbps over multimode fiber cable.
- 1000BaseBX - 1000 Mbps over single mode fiber cable.
The Ethernet standards continue to evolve. with 10 Gigabit Ethernet (10,000 Mbps) and 100 Gigabit Ethernet (100,000 Mbps),
Ethernet Protocol Summary
| Protocol |
Cable |
Speed |
| Ethernet |
Twisted Pair, Coaxial, Fiber |
10 Mbps |
| Fast Ethernet |
Twisted Pair, Fiber |
100 Mbps |
| Gigabit Ethernet |
Twisted Pair, Fiber |
1000 Mbps |
|
LocalTalk
LocalTalk is a network protocol that was developed by Apple Computer, Inc. for Macintosh computers many years ago. LocalTalk adapters and special twisted pair cable can be used to connect a series of older computers through the serial port (current Macintosh computers have Ethernet cards and/or wireless adapters installed). A primary disadvantage of LocalTalk is speed. Its speed of transmission is only 230 Kbps.
Token Ring
The Token Ring protocol was developed by IBM in the mid-1980s. The access method used involves token-passing. In Token Ring, the computers are connected so that the signal travels around the network from one computer to another in a logical ring. A single electronic token moves around the ring from one computer to the next. If a computer does not have information to transmit, it simply passes the token on to the next workstation. If a computer wishes to transmit and receives an empty token, it attaches data to the token. The token then proceeds around the ring until it comes to the computer for which the data is meant. The Token Ring protocol requires a star-wired ring using twisted pair or fiber optic cable. It can operate at transmission speeds of 4 Mbps or 16 Mbps. Due to the increasing popularity of Ethernet, the use of Token Ring in school environments has decreased dramatically.
IP and IPX (Network Layer)
The network layer is in charge of routing network messages (data) from one computer to another. The common protocols at this layer are IP (which is paired with TCP at the transport layer for Internet network) and IPX (which is paired with SPX at the transport layer for some older Macintosh, Linus, UNIX, Novell and Windows networks). Because of the growth in Internet-based networks, IP/TCP are becoming the leading protocols for most networks.
Every network device (such as network interface cards and printers) have a physical address called a MAC (Media Access Control) address. When you purchase a network card, the MAC address is fixed and cannot be changed. Networks using the IP and IPX protocols assign logical addresses (which are made up of the MAC address and the network address) to the devices on the network, This can all become quite complex -- suffice it to say that the network layer takes care of assigning the correct addresses (via IP or IPX) and then uses routers to send the data packets to other networks.
TCP and SPX (Transport Layer)
The transport layer is concerned with efficient and reliable trsansportation of the data packets from one network to another. In most cases, a document, e-mail message or other piece of information is not sent as one unit. Instead, it is broken into small data packets, each with header information that identifies its correct sequence and document.
When the data packets are sent over a network, they may or may not take the same route -- it doesn't matter. At the receiving end, the data packets are re-assembled into the proper order. After all packets are received, a message goes back to the originating network. If a packet does not arrive, a message to "re-send" is sent back to the originating network.
TCP, paired with IP, is by far the most popular protocol at the transport level. If the IPX protocol is used at the network layer (on networks such as Novell or Microsoft), then it is paired with SPX at the transport layer.
HTTP, FTP, SMTP and DNS (Session/Presentation/Application Layers)
Several protocols overlap the session, presentation, and application layers of networks. There protocols listed below are a few of the more well-known:
- DNS - Domain Name System - translates network address (such as IP addresses) into terms understood by humans (such as URLs)
- DHCP - Dynamic Host Configuration Protocol - can automatically assign Internet addresses to computers and users
- FTP - File Transfer Protocol - a protocol that is used to transfer and manipulate files on the Internet
- HTTP - HyperText Transfer Protocol - An Internet-based protoco